Staying ahead in cyber security: Strategies part 2
In part one of this blog series, we discussed some of the platform policies that you can put in place to minimise your risks. It is now time to...
4 min read
CPiO Limited : Apr 16, 2024 11:05:00 AM
Cyber security is an ever-moving target, IT departments need to have continued access training to obtain new skills and knowledge to keep up to date with new threats that are being created by cyber criminals all the time. Unfortunately cyber threats are only going to increase.
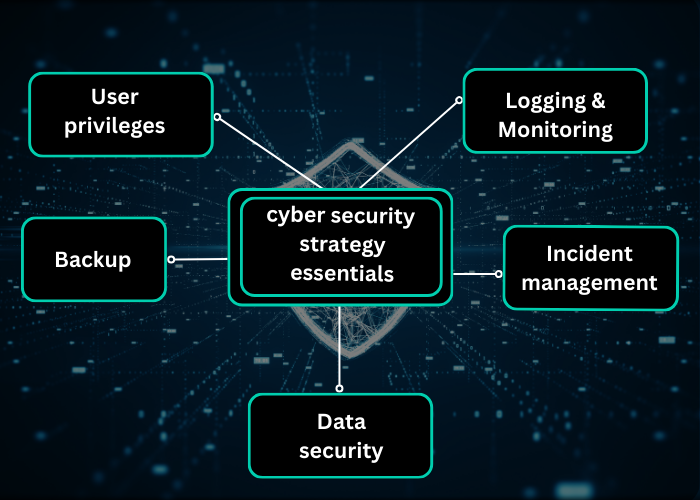
Risk management within the cyber security domain helps to ensure that the software, technology, systems, and information within your organisation are protected. A good risk management approach will be embedded throughout your organisation and complement the way you manage other business risks. Remember that risk management is a consistent process and as technology changes, so does the business environment and your associated threats and opportunities.
Is your business network secure?
Once there is a good understanding about how the business operates from the IT department, the next step is to review your network security, which shares the information throughout the business and is accessed by end-users. This starts by determining who has access to parts of the network to assist with their daily tasks and how these users are monitored whilst on the network. By managing who is accessing your business network and what they can access, this provides a block for any attackers, and they will struggle to pretend that they are legitimate employees whilst ensuring that any employees who do access the network are still able to access what they need to.
It is important to consider how you establish all employees' identities when they are accessing your business network, by ensuring that your organisation implements identity and access management policies, this ensures that only those who are authorised can access certain routes within the business network which lessens the risk of a cyber attack.
Another process which is beneficial for cyber security is the implementation of a ‘joiners, movers, and leavers’ policy, where access can be revoked from anyone who leaves your organisation or for an individual that is employed on a temporary basis or changed for any employee who moves around the business e.g. for promotion or a job change.
.png?width=792&height=264&name=joinermoverleaverrule%20(1).png)
Is your logging system efficient enough?
‘Collecting logs’ or collecting different entries within your organisations and storing them in one place is essential to understand how your systems are being used and is the foundation of security monitoring. In the event of a (potential) cyber attack, logging practices will allow you access data that you have previously stored to analyse, observe and compare.
When designing a log collection or a monitoring solution, it should be proportionate to the context of the system, the threat that your organisation faces and the resources available to you. It is important to store these logs efficiently to ensure that those with access can find them quickly and identify when and where previous activity has occurred.
Also, it is important to consider what parts of your organisation need to be monitored, this should include your network, devices and cloud services if applicable. Any monitoring solutions that are implemented should include signature-based capabilities to detect known attacks, and heuristic capabilities to detect unusual user system behaviour.
Many organisations only realise their logging and monitoring systems are broken or insufficient when an actual incident occurs so active exercising can help to avoid whilst this allowing you to improve your systems. Find out more.

Do you know that only 45% of companies have an incident response plan in place?
 Cyber incidents can have a great impact on an organisation in terms of cost, productivity and reputation.
Cyber incidents can have a great impact on an organisation in terms of cost, productivity and reputation.
IT departments should create an Incident Response Plan. This ensures forward planning and can help to minimise cyber attacks. Senior management should support and provide input to critical decisions and all employees should be provided with regular cyber training to detect incidents. The Incident Response Plan should align with your organisations current methods of detection including logging, monitoring and reporting. Plans need to also include a rigid and thorough criteria for escalation if any incidents do occur.
By identifying specific situations where IT departments can act autonomously, based on the highest business risks, this is likely to reduce the impact cyber incidents. IT departments should practice restoring files from backups too so that after an incident, only clean data is copied back onto clean systems and networks. The Incident Response Plans should be updated after every incident whether also.
Don't leave it until you have suffered a cyber attack. Talk to one of CPiO's technical security experts who can advise you on policy and solutions.
How can you ensure effective data protection against unauthorised access?
It is critical for any data within your organisation to be protected from unauthorised access, modification, or deletion.
You should ensure that data is protected in transit so that it cannot be viewed by unauthorised users or interfered with, any unencrypted communications can provide opportunities for attackers to capture sensitive data or move it onto their own networks by spoofing a service.
Any data that you no longer need shouldn’t be stored within your business network and data that you do need should be consolidated where possible to make it easier to secure, protect and manage. By implementing physical and logical access controls, only authorised users can access and/or modify your data which lowers the risk of tampering or interference. It is also advised to apply disk encryption for devices and removable media, which should be used where there is a risk of physical theft and loss.
If others are storing your data, then there should be a consideration of where this is, for example cloud services, supply chains or on employees personal devices. Security measures should be implemented protect this data and perhaps assurances added that you need to seek from third parties.
It is important to have multiple backups of important data files that should be stored in different locations. The ‘3-2-1’ rule is a good strategy to use, this is the idea of having data stored on at least 3 copies, on 2 devices, and 1 offsite backup.
.png?width=1200&height=400&name=Backup%20rule%20(1).png)
Your backup data should be regularly tested to ensure that you are aware of how to access it should you need to in a real situation and ensures you can gain access to your backups in the event of a system failure. It is also important to note that malware may persist in backups, so you should ensure files are scanned using up to date antivirus software when they are being restored.
Cyber criminals are becoming more sophisticated, cyber attacks and scams are being created every day. It is important for you to understand and implement a variety of prevention techniques from storing data safely and ensuring only those who need to access data do, to training and educating all employees, this can help to ensure safety within your organisation and mitigate the risk of a cyber attack.
At CPiO, we understand the critical role that technical expertise plays in safeguarding businesses from cyber threats. Explore our dedicated IT & cyber security services to discover the comprehensive range of services we offer and how we can help safeguard your business against cyber threats.
Don't leave it until you have suffered a cyber attack. Talk to one of CPiO's technical security experts who can advise you on policy and solutions.
Keep up to date with CPiO's latest blogs, news and events

In part one of this blog series, we discussed some of the platform policies that you can put in place to minimise your risks. It is now time to...

With a high level of fraudulent emails and illicit messages circulating at present, some under the guise of NHS and Government Covid-19...

The way we work has undergone a dramatic shift. Cloud applications, remote workforces, and the ever-growing threat landscape demand a new approach to...